SSL Certificate Monitoring With CertAlert
This article explains how to setup SSL certificate monitoring with CertAlert Today, most organisations have many servers to manage and a large percentage of these typically run one or more services over SSL; examples include: SMTP, HTTP, POP3, FTP, LDAP, and NNTP. The expiration of an SSL certificate can have very serious consequences for an organisation including downtime, loss of productivity, and loss of customer confidence.
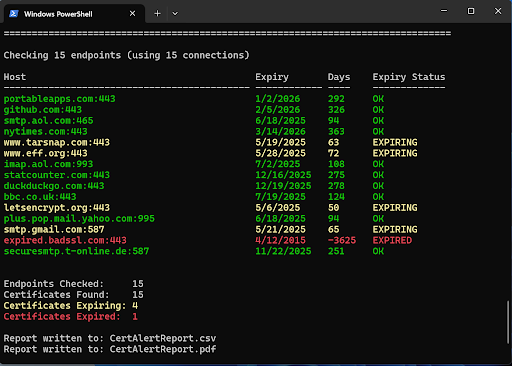
Performing an SSL certificate scan with CertAlert
CertAlert performs many functions essential to SSL certificate monitoring. These include:
- SSL Certificate Discovery
- SSL Certificate Information Gathering
- SSL Certificate Expiration Monitoring and Alerting
To configure an SSL scan with CertAlert you should:
- Specify the IP Address Ranges or alternatively a list of hostnames to scan.
- Set the ports you wish to scan.
for example: 192.168.1.1-254,192.168.2.1-180,192.168.3.1-100,192.168.0.0/24
for example: 1-65,443,444,4000,45000-45500
These two steps show how to quickly perform a scan and obtain a report. However, you can configure many other settings in CertAlert such as: report emails, alert emails, warning intervals, reverse lookup, expiry states to report, and several others.
Analysis of an SSL certificate scan
When you run CertAlert, it will create a report file called CertCheckerReport.csv. This file provides detailed information on the certificates discovered. Using this report, we can carry out several important checks which are discussed below.
Have any SSL certificates expired?
An expired certificate can have serious consequences for your organisation. Browsers will typically flag web servers with expired certificates as untrusted; this can lead to a lack of credibility for your organisation. Applications that communicate securely over SSL will stop working if the application's certificate is left to expire; this can result in delayed transactions and financial loss.
Are SSL certificates using short keys?
Are there any certificates with key sizes less than 2048 bits? NIST recommends that a minimum key size of 2048 bits should be used.
Are SSL certificates using weak signature algorithms?
The signature algorithm md5RSA, uses the weak hashing algorithm MD5. The report identifies the signature algorithm used for each certificate so it's easy to check if a weak algorithm like md5 is being used.